IoT

The dataset contains a collection of V2X (Vehicle-to-Everything) messages for classification, prioritization, and spam message detection. It comprises 1,000 messages with varying message types, content, priorities, and spam labels. The messages are sourced from different vehicles with specific destination vehicles or broadcast to all vehicles. They cover various message types, including traffic updates, emergency alerts, weather notifications, hazard warnings, roadwork information, and spam messages. The priority of the messages is categorized as either high, medium, or low.
- Categories:
 620 Views
620 Views
This dataset consists of high-resolution visible-spectrum (RGB) and thermal infrared (TIR) images of two vineyards (Vitis vinifera L.) with varieties of Mouhtaro and Merlot, which was captured by Unmanned Aerial Vehicle (UAV) carrying TIR and RGB sensors three times in a cultivation period.
- Categories:
 508 Views
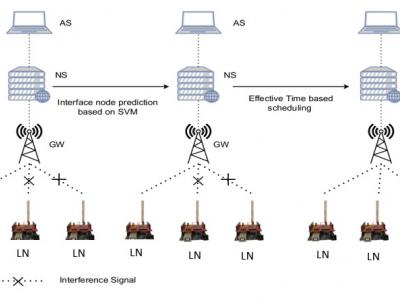
508 ViewsTo illustrate the impact of the obstacles, we consider indoor and outdoor scenarios. We consider the Department of Computer Science and Engineering, IIT(BHU) buildings as indoor buildings and the railway platform as an outdoor scenario. Here, we use single-channel LG in our experiment. The distance between LNs and LG varies from 5 to 50 meters. The floor map illustrates the walls, doors, and windows between LNs and LG. We consider railway stations for the outdoor environment. The outdoor environment did not consist of obstacles between LNs and LG.
- Categories:
 227 Views
227 ViewsThe dataset contains basketball activity data for nine varsity basketball players of professional skill levels. Each player wore a smart bracelet on their right wrist to record activity data during the event. The smart bracelet contains an accelerometer and gyroscope that collects acceleration and angular velocity information, and it has a sampling frequency of 50 Hz. The basketball activities of the players are laying up, passing and shooting, which are defined as shown in Table 1.
- Categories:
 40 Views
40 Views
Physical layer security (PLS) is seen as the means to enhance physical layer trustworthiness in 6G. This work provides a proof-of-concept for one of the most mature PLS technologies, i.e., secret key generation (SKG) from wireless fading coefficients during the channel’s coherence time. As opposed to other works, where only specific parts of the protocol are typically investigated, here, we implement the full SKG chain in four indoor experimental campaigns.
- Categories:
 327 Views
327 ViewsCattle health monitoring is essential in the modern world, because of the high demand for dairy products. Regular monitoring is essential to extend the lifecycle of cattle and maintain the quality of dairy products. Unfortunately, Observing the health of cattle regularly is difficult in large farms where workers do not have enough time to do so. This paper described IoT devices such as skin temperature, heart rate, and motion sensor. Using this device, you can monitor cattle’s heart rate, activity level, heat stress, the surrounding temperature, and sleep tracking.
- Categories:
 1421 Views
1421 Views
In this investigation, the researchers have used a commercially available millimeter-wave (MMW) radar to collect data and assess the performance of deep learning algorithms in distinguishing different objects. The research looks at how varied ambiance factors, such as height, distance, and lighting, affect object recognition ability in both static and dynamic stages of the radar.
- Categories:
 454 Views
454 Views
Sales data collection is a crucial aspect of any manufacturing industry as it provides valuable insights about the performance of products, customer behaviour, and market trends. By gathering and analysing this data, manufacturers can make informed decisions about product development, pricing, and marketing strategies in Internet of Things (IoT) business environments like the dairy supply chain.
- Categories:
 1807 Views
1807 Views
Smart home automation is part of the Internet of Things that enables house remote control via the use of smart devices, sensors, and actuators. Despite its convenience, vulnerabilities in smart home devices provide attackers with an opportunity to break into the smart home infrastructure without permission. In fact, millions of Z-Wave smart home legacy devices are vulnerable to wireless injection attacks due to the lack of encryption support and the lack of firmware updates.
- Categories:
 131 Views
131 Views