Security
An IEEE 802.15.4 backscatter communication dataset for Radio Frequency (RF) fingerprinting purposes.
It includes I/Q samples of transmitted frames from six carrier emitters, including two USRP B210 devices (labeled as c#) and four CC2538 chips (labeled as cc#), alongside ten backscatter tags (identified as tag#). The carrier emitters generate an unmodulated carrier signal, while the backscatter tags employ QPSK modulation within the 2.4 GHz frequency band, adhering to the IEEE 802.15.4 protocol standards.
- Categories:
 167 Views
167 ViewsX-CANIDS Dataset (In-Vehicle Signal Dataset)
In March 2024, one of our recent research "X-CANIDS: Signal-Aware Explainable Intrusion Detection System for Controller Area Network-Based In-Vehicle Network" was published in IEEE Transactions on Vehicular Technology. Here we publish the dataset used in the article. We hope our dataset facilitates further research using deserialized signals as well as raw CAN messages.
Real-world data collection. Our benign driving dataset is unique in that it has been collected from real-world environments.
- Categories:
 203 Views
203 Views
This dataset is associated with the injection of false data into solar-powered insecticidal lamps, primarily aimed at reporting false data injection attacks on the Solar insecticidal lamps-Internet of Things (SIL-IoTs). The data was collected on the campus of Nanjing Agricultural University, gathering two types of data from the insecticidal lamp device of Chengdu Biang Technology Co., Ltd. and our team's self-developed insecticidal lamp device (insect count and sound signal data, respectively). The insect count data is in text format and has not been processed.
- Categories:
 14 Views
14 Views
Image representation of Malware-benign dataset. The Dataset were compiled from various sources malware repositories: The Malware-Repo, TheZoo,Malware Bazar, Malware Database, TekDefense. Meanwhile benign samples were sourced from system application of Microsoft 10 and 11, as well as open source software repository such as Sourceforge, PortableFreeware, CNET, FileForum. The samples were validated by scanning them using Virustotal Malware scanning services. The Samples were pre-processed by transforming the malware binary into grayscale images following rules from Nataraj (2011).
- Categories:
 61 Views
61 ViewsIn today's world of online communication, hate speech is a big problem. This dataset focuses on hate speech in Bengali, analyzing speeches to see if they contain hate or not. While there are many ways to analyze text online, most of them focus on languages like English, leaving out Bengali. But hate speech in Bengali is serious and common, especially on platforms like Facebook and YouTube. Sometimes, even TV shows have comments that are not nice for everyone to see. Finding and stopping hate speech in Bengali is hard because there aren't good tools for it yet.
- Categories:
 137 Views
137 ViewsGNSS recordings on four distinct scenarios to evaluate the Galileo Open Service Navigation Message Authentication (OSNMA) protocol with different receiver optimizations. However, the recordings are generic and can be used for any other GNSS purpose as they contain PVT measurements and data for GPS, Galileo, Glonass, and BeiDou.
- Categories:
 132 Views
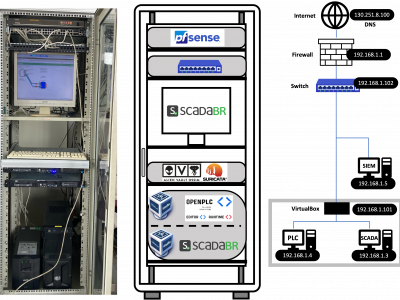
132 ViewsThe increasing integration of cyber-physical systems in industrial environments has under scored the critical need for robust security measures to counteract evolving cyber threats. In response to this need, this work introduces an open-source dataset designed to enhance the development and evaluation of cybersecurity solutions for smart industries. The dataset comprises a traffic capture of an industrial control system (ICS) subjected to a variety of simulated cyber-attacks, including but not limited to denial of service (DoS), man-in-the-middle (MITM), and malware infiltration.
- Categories:
 195 Views
195 Views
This research utilizes real-world malware samples that are reinforced with the latest VM-based packers and digitally signed to ensure runtime execution. For academic research purposes only, these packed malware samples are provided as running instances to facilitate behavioral, forensic and detection analysis. Users are forewarned on the potential risks of executing unknown malicious programs, and should refrain from installing or propagating these files outside of a controlled experimental environment.
- Categories:
 119 Views
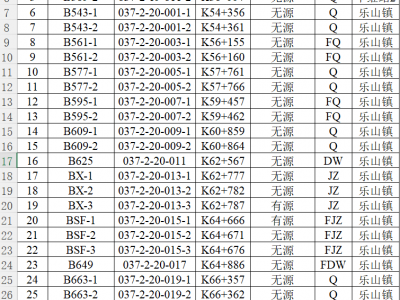
119 ViewsCTCS-2 level train control engineering data is primarily categorized into trackside infrastructure data and line parameters, including line velocity table, line gradient table, line broken chain detail table, balise position table, main line signal data table and so on. The dataset image above is an example of a balise position table.
- Categories:
 180 Views
180 Views
This dataset includes input dynamics (keystroke, touch, and mouse), affect data (physiological measurements), video, and text data collected from research participants aged 6 and older. The dataset includes data from a diverse set of participants, identifying as Asian, White, Middle Eastern or North African, Black or African American, and Hispanic, Latino, or of Spanish origin). Additionally, participants represent both iOS and Android users.
- Categories:
 121 Views
121 Views